Identify Threat Actors that Use Azure Storage Tools to Ransom Sensitive Data

The blog post “Highway Blobbery: Data Theft Using Azure Storage Explorer” (ModePush, 2024) highlights how threat actors exploit legitimate tools like Azure Storage Explorer and AzCopy for data exfiltration. Attackers leverage these tools to transfer large datasets from compromised environments, often bypassing traditional detection methods.
Understanding Azure Storage Explorer and AzCopy
Azure Storage Explorer is a graphical tool for managing Azure storage accounts. It allows users to view, upload, download, and delete files in blob storage, file shares, and other Azure storage resources. It offers an easy-to-use interface for handling data stored in the cloud, making it popular for legitimate administrative tasks.
AzCopy, on the other hand, is a command-line utility designed for high-speed data transfer between local environments and Azure storage. It’s ideal for automating bulk uploads, downloads, and data migrations.
Why they’re attractive to attackers
Because both Azure Storage Explorer and AzCopy are legitimate Microsoft tools with powerful data transfer capabilities, ransomware attackers can misuse them to exfiltrate large amounts of data from compromised systems without raising suspicion.
Using KQL queries to detect misuse of AzCopy and Azure Storage Explorer
By leveraging Kusto Query Language (KQL) in tools like Microsoft Sentinel or Microsoft Defender for Endpoint, security teams can proactively hunt for suspicious activity related to the AzCopy and Azure Storage Explorer misuse. Here are some examples of KQL queries that could help identify potential threats:
Detect unauthorized use of AzCopy
This query monitors for any usage of the AzCopy command by unapproved users or at unusual times, such as outside business hours.
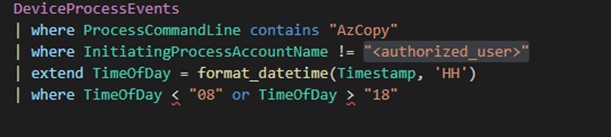
What It Does: Looks for processes where the command line includes “AzCopy,” checks if the initiating user is not an authorized account, and flags executions that occur outside of typical working hours.
Monitor unusual data transfers with AzCopy
This query focuses on identifying large-scale data uploads to Azure Blob storage using AzCopy.
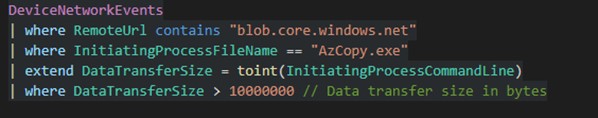
What It Does: Filters for outbound network connections to Azure Blob storage by tracking traffic originating from AzCopy.exe and flags large data transfers.
Spot suspicious activity in Azure Storage Explorer
This query identifies unusual usage of Azure Storage Explorer based on user behavior or abnormal access patterns.
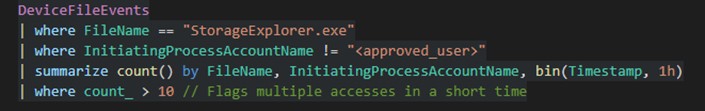
What It Does: Monitors Storage Explorer execution by non-approved users and detects multiple or unusual accesses within a short time window.
Detect remote data exfiltration
This query tracks any large data downloads or uploads via Azure Storage Explorer or AzCopy to external Azure Blob endpoints.
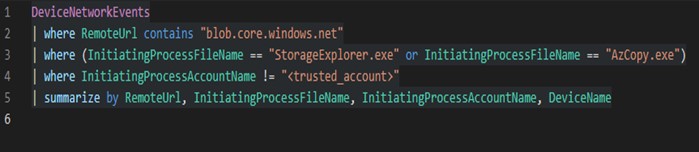
What It Does: Combines the tracking of Storage Explorer and AzCopy traffic to blob storage endpoints and filters out trusted accounts, providing insights into potential data exfiltration activities.
By using these queries, security teams can spot and respond to unauthorized use of AzCopy or Azure Storage Explorer, helping prevent data theft and secure cloud environments. Implementing these queries in Microsoft Sentinel alongside Defender for Endpoint strengthens monitoring capabilities and helps organizations stay one step ahead of malicious actors.
Partner with ArcherPoint for endpoint security
Securing endpoints from the exploitation of tools like Azure Storage Explorer requires expert planning. ArcherPoint can help set up Microsoft Defender for Endpoint, apply application controls, and configure Entra ID to ensure that your organization is protected against such attacks. Additionally, ArcherPoint provides GRC services to ensure full compliance with data security regulations.
By focusing on endpoint security and monitoring, your organization can effectively mitigate risks associated with legitimate tools like Azure Storage Explorer.
Contact ArcherPoint to learn more.
Trending Posts
Stay Informed
Choose Your Preferences
"*required" indicates required fields
