How To Use Visual Studio Code to Create Cybersecurity Defense Playbooks for Routine Preventative and Detection Tasks

When performing IT maintenance and identifying issues from a cyber-risk/cyber-defense perspective, you can use playbooks. Users can create playbooks easily using Visual Studio and can be used for a variety of system administrative tasks. In this blog, we discuss how create playbooks for routine preventative and detective tasks related to cybersecurity defense.
How Microsoft Used the Power of Notebooks to Create an Interactive Experience
Jupyter Notebooks in the past was a mostly Python-exclusive extension. With the creation of MSTICPy (pronounced “mystic pie”), a Python library designed for authoring Jupyter Notebooks in Azure Sentinel. Jupyter Notebooks works inside the Azure Sentinel workspace; however, the notebook inside the Azure Sentinel workspace only works on Python kernels, so you must use Python to run those notebooks.
Microsoft recently expanded on the use of Notebooks by making the Jupyter Notebook format compatible with some of the Microsoft languages with an extension called “.NET Interactive” (formerly known as Try.Net). Once installed, users get access to Interactive Notebooks from Visual Studio code. There are many free tools anyone can use. One great feature of Interactive Notebooks and Visual Studio Code is that, in the command palette, you have the option of languages that should be more familiar to Microsoft developers, such as C#, F#, PowerShell (Figure 1), and so on. You are not forced to use Python, but you could use Python if you want to. You can also use HTML, JavaScript, Kusto Query, SQL, or several other tools as well.
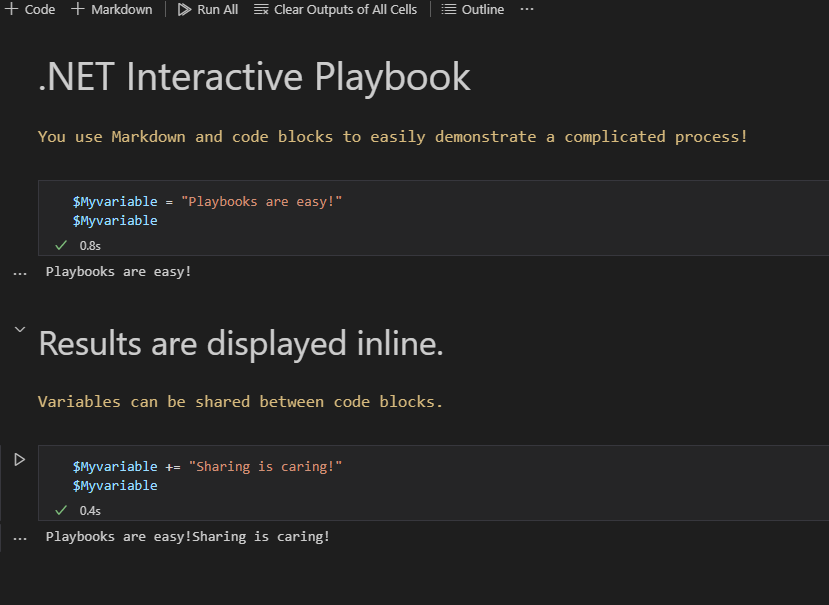
Notebooks can contain text, graphics, executable code, and code results. This allows technical resources to develop playbooks for a variety of uses, offering step-by-step guidance for less technical staff. For example, a playbook can be created to check if a database instance is running. Text can explain the steps to take along with code to execute to see if (a) a network connection is running and (b) the target database instance is running.
Another convenient feature of a Notebook is Markdown, an easy-to-use markup language that provides a quicker, easier way to define an outline for a document you are writing, as well as making the playbooks exceptionally clean. You can generate an outline of steps with an explanation of what you are doing, and even introduce a block of executable code. Then you can “roll up” these sections to make the document easier to read. Sections can be expanded as the reader works through the steps of the document. Along the way, the code snippets can be executed. The document can also show the results as the code is executed. Section roll-ups are handy for experienced users who do not need detailed instructions for a specific task or choose to skip over optional tasks, avoiding the problem of scrolling through a 10-page Word document trying to find the instructions they need.
Uses for Interactive Notebooks in Cybersecurity
Notebooks can be used in a multitude of ways. At ArcherPoint, one use case is to create playbooks to automate common security monitoring for IT. These tools can be used to set up routine checks, offering step-by-step guidance to check for malicious code, spam, phishing attempts, messages from known bad domains, and more. The more serious issues will require human intervention, but using notebooks in this way will capture most of the low hanging fruit where the majority of attacks occur, making the most use of the security administrator’s time.
Interactive Notebooks are ideal for writing playbooks that automate routine activities that identify and address potential cybersecurity threats for Blue Team defense. For example, Figure 2 shows the contents of a playbook for detecting possible phishing attacks.
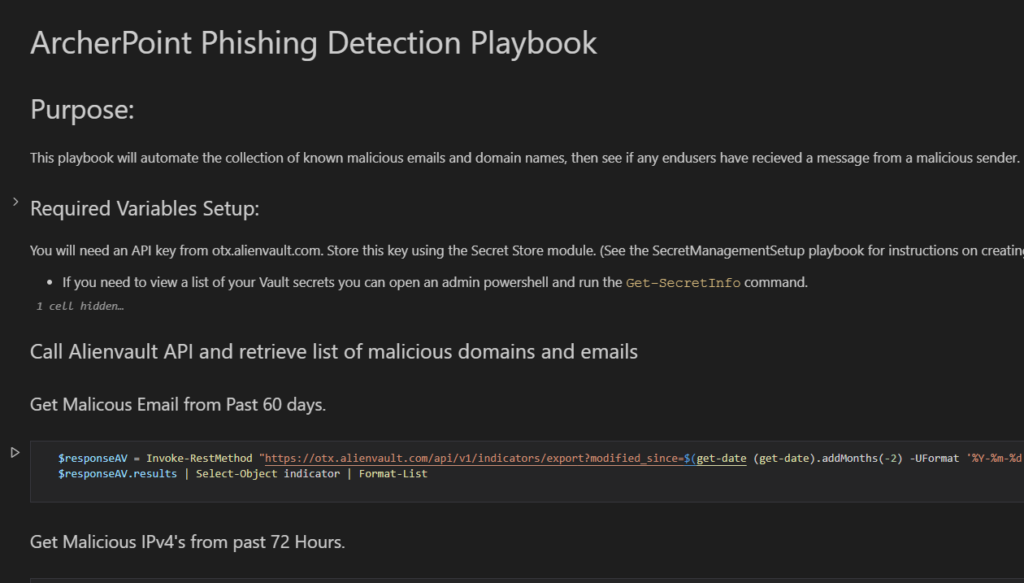
In this example, the playbook pulls a list of malicious domains and emails and then runs a message trace to see if anyone within our organization has received an email from that domain or a known malicious sender. As the figure shows, each step is sectioned off and can be expanded for step-by-step instructions and with code examples.
As another example, we could make a playbook for mail header forensics. This would allow a user to quickly run through emails, pull out the key information, and test it. Run a file, hash pass virus total, run a domain name through AlienVault, and finally run an SPF check. Playbooks can be used to do all that.
Expanding the Use of Playbooks
From a perspective of IT Managed Services, these types of playbooks can be written and implemented in almost any environment as an onboarding guide. That way, people on the security operations team who are just learning the company’s security setup have detailed instructions – click here, enter this comment, verify that configuration, etc.
With the increased risk and stress and strain on IT departments to keep their companies safe, playbooks help keep IT security staff stay focused on the things that need their attention most: guarding against new threats and new tactics to gain access to their systems.
Find Out More About Interactive Notebooks
To learn more about using Interactive Notebooks, check out these resources from Microsoft:
- Get started with Jupyter notebooks and MSTICPy in Microsoft Sentinel
- How to Use .NET Interactive Jupyter Notebooks in Daily Work-Life
- Use playbooks with automation rules in Microsoft Sentinel
- Run Jupyter Notebooks in your workspace
Let Us Help You with Cybersecurity and More
If you need help managing Azure, Dynamics 365 Business Central, Microsoft 365, or other Microsoft solutions, ArcherPoint offers Managed IT Services for businesses running Microsoft Dynamics 365 Business Central. Contact us today to get started.
To learn more about cybersecurity, watch our webinar Demystifying Cybersecurity with ArcherPoint, where we pack a lot into 30 minutes, including endpoint management, password health, backups, end user education, and more.
