Password Security and Protection Has Never Been More Important

How secure is your password?
For years, the rule has been to use a complex password – the more complex the password, the more challenging it was for a hacker to access your account. Of course, that’s assuming they know your user ID, which, for many accounts, is your email. Password complexity is a function of how many characters you use and whether you include a combination of upper- and lower-case letters with numbers and symbols.
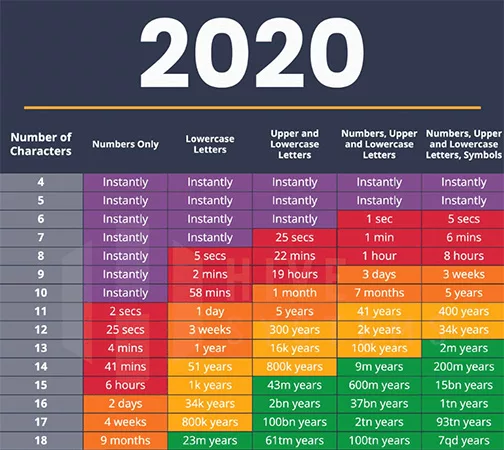
Until recently, that seemed reasonable. According to the cybersecurity company Hive Systems, a relatively complex password of nine characters using numbers, mixed-case letters, and symbols would take a hacker three weeks to crack using brute force…in 2020.
This table was based on the processors and software that were readily available in 2020 and could be used to crack passwords using brute force.
In 2023, that table has changed substantially:
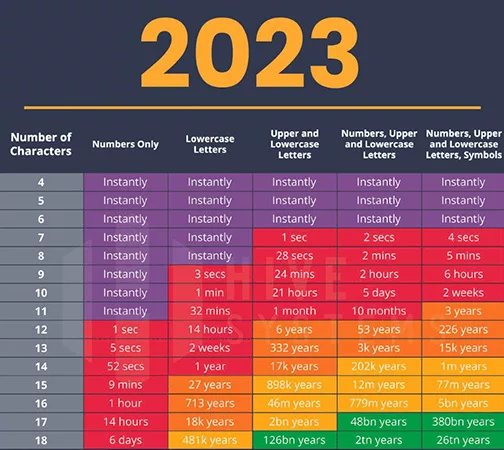
Today, that 9-character password that took three weeks to crack now only takes six hours. That assumes the hacker uses high-end consumer graphics cards you can buy at BestBuy or Amazon, such as nVidia 2080ti in 2020 and 4090 in 2023. Once they step up to server-grade hardware like A200 GPUs and AI-assisted models and bots to do the brute force password cracking, cracking a complex 9-character password could only take one minute!
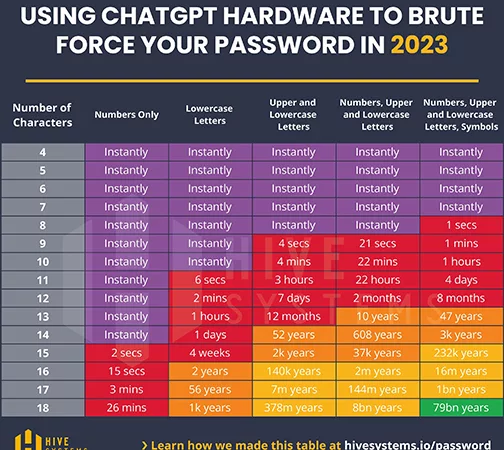
As processors and tools become faster in the future, even a complex password will become less and less secure.
The best advice is to choose a complex password of at least 12 characters and never use the same password for multiple accounts. To avoid using a single, easy-to-remember password for all your accounts, many security experts recommend using a password manager to keep your passwords secure. However, critics caution that password managers are only as safe as the master password you use.
Still, password managers are valuable tools and the only way most people can have unique, complex passwords for all their online accounts. It becomes the lesser of the two evils.
Other suggestions include:
- Use a passphrase, a 4-5 random word combination with spaces, as your password because the length trumps complexity.
- Reducing reused passwords is the best thing you can do to protect yourself.
- Most password managers have Multi-Factor Authentication (MFA, see below); you should always opt in for the added protection.
How do bad actors get your password?
A common way bad actors attempt to gain access is to try multiple combinations (brute force), hoping they will stumble on a combination that works.
A refinement of the brute force method is to try a series of commonly used passwords or phrases, hoping one is correct.
Yet a different tactic is to acquire a list of usernames obtained from a data breach and use a single, commonly used password against each username.
Sadly, each process can be automated, saving the hacker time and energy.
As it turns out, brute force represents only a small percentage of attacks. Phishing and social engineering account for nearly 80% of password breaches. Once the hacker has your login credentials, they will try to use it against other websites, such as social media, banks, and credit cards, hoping you repeat your passwords across your accounts. Having a password manager reduces how far and wide attackers can go with stolen credentials.
Making your passwords stronger with multi-factor authentication
Multi-factor authentication (MFA) is a process that uses more than one authentication method.
Two-factor Authentication (2FA) is a common form of MFA that makes the login process more secure. Using 2FA, simply entering your username and password is not enough. Once you successfully enter your credentials to log into a site, the site will send you a code through other means to verify that it is you, using methods such as text message, biometrics (fingerprint on your phone), or email. This way, the hacker will need access to your phone or email to complete the login process. While not foolproof, 2FA adds an extra layer of protection, making hacking much more difficult. In addition, 2FA is easy for the user to use and relatively inexpensive to implement.
The drawback to 2FA is that it is usually tied to a person’s mobile phone. If the hacker has access to your phone, they typically have access to your email and text messages, meaning they will receive the code needed to complete the login. They also can access any accounts or apps your phone might be logged into.
Even without access to your phone, hackers can still bypass 2FA. SMS (text) messaging is a common 2FA technique. Text messages are transmitted using unencrypted channels and can be easily intercepted and read.
Hackers have even used a combination of data leaks, social media profiles, and social engineering to get a target’s phone number and then leveraged that information to social engineer the phone company to transfer the target’s phone number to a SIM card in a phone they control, a technique called SIM swapping, letting them receive the text verification codes and break into the target’s accounts.
Using authenticator apps
Authenticator apps, such as Google and Microsoft, provide an even more reliable form of authentication than the typical 2FA using text messages. With an authenticator app, users first pair their mobile device with the account, so only that device can be used to authenticate. Once they enter their login credentials, users receive a code they must enter before login access is granted. The advantage is that the app communicates directly with the phone and does not rely on unsecured SMS transmission. SIM swapping will not work in this scenario because the app only works with the user’s phone. Changing phones requires the user to pair the new device with the app.
Microsoft even allows passwordless login to Microsoft accounts using its Authenticator app.
Utilizing conditional access policies
Organizations should not rely on MFA alone and should also set up additional methods of authentication that rely on Conditional Access policies to make access more “phish-resistant”.
For example:
- If an employee is based in the United States and there is no reason why they should be accessing the system from outside the country, a conditional access policy can notify the administrator for authorization before granting access.
- A conditional access policy can be used to prevent logins from using the same user credentials from two different parts of the world.
- A conditional access policy can be set up to prevent logins for employees after business hours without administrator approval.
Conditional Access policies can narrow down logins for one location, device, IP Address, application, and individual, if necessary.
Recap
To sum up:
- Choose a strong password.
- Don’t reuse your password.
- Use a reliable password manager.
- Be aware of phishing and social engineering tactics.
- Use two-factor authentication whenever possible.